Secrets Management
Overview
Secrets in Swiftor are encrypted environment variables accessible within your VMs. Use them to store sensitive data like API keys, passwords, and tokens securely.
Managing Secrets
Adding Secrets
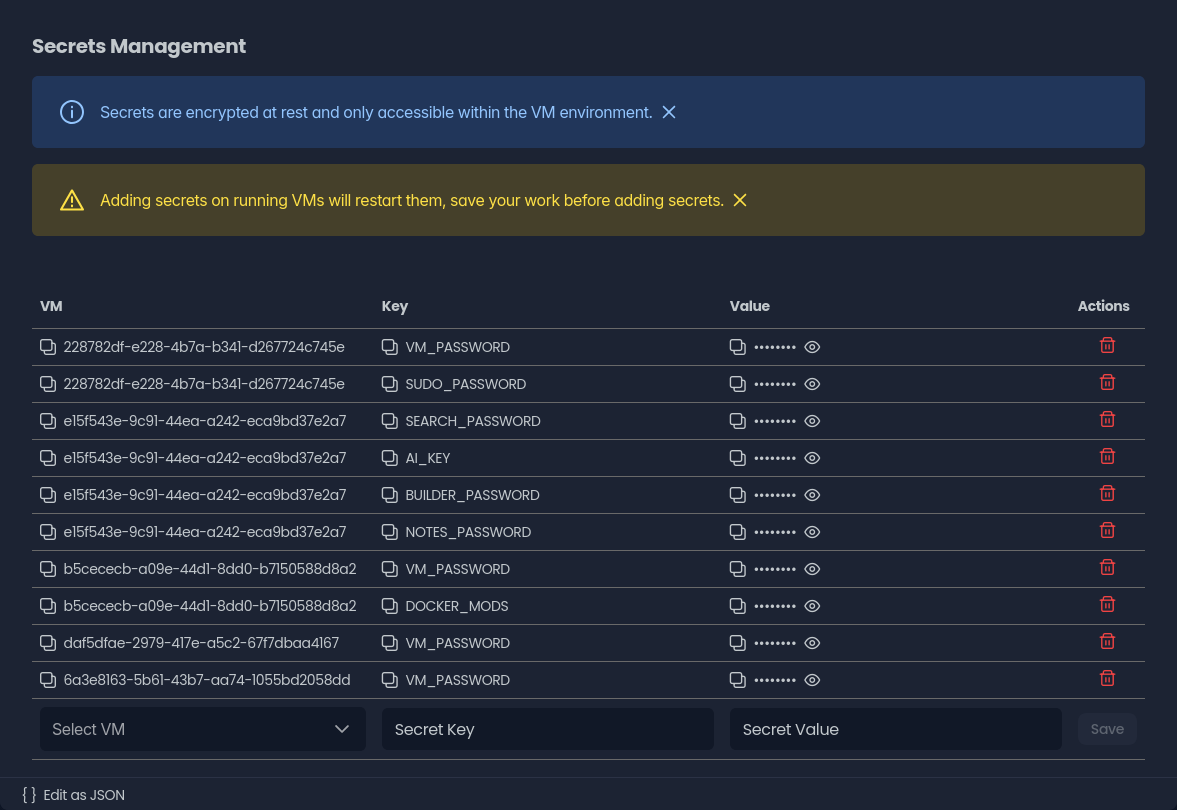
The secrets manager shows a table with all your VM secrets:
| Column | Description |
|---|---|
| VM | Target virtual machine |
| Key | Environment variable name |
| Value | Secret value (encrypted) |
| Actions | Copy/Delete options |
[gif: Adding a new secret]
Bulk Import
Use the JSON editor for bulk secret management:
{
"vm-id": {
"API_KEY": "your-api-key",
"DB_PASSWORD": "database-password",
"JWT_SECRET": "jwt-secret-key"
}
}JSON Format
Each VM can have multiple key-value pairs. All values must be strings.
Accessing Secrets
Your secrets are available as environment variables inside the VM. Here's how to access them in different languages:
Bash
# Read API key
echo $API_KEY
# Use in commands
curl -H "Authorization: Bearer $API_KEY" https://api.example.comPython
import os
# Get single secret
api_key = os.getenv('API_KEY')
# Get multiple secrets
config = {
'db_user': os.getenv('DB_USER'),
'db_pass': os.getenv('DB_PASSWORD')
}JavaScript/Node.js
// Access secrets
const apiKey = process.env.API_KEY;
const dbConfig = {
user: process.env.DB_USER,
password: process.env.DB_PASSWORD
};Security Notes
Security Considerations
- Secrets are encrypted at rest
- Only accessible within the VM
- Not visible in VM logs
- Automatically rotated on VM rebuild
Common Use Cases
API Configuration
API_KEY: your-api-key
API_SECRET: your-api-secret
API_ENDPOINT: https://api.service.comDatabase Credentials
DB_HOST: database.host
DB_USER: admin
DB_PASSWORD: secure-passwordJWT Authentication
JWT_SECRET: your-jwt-secret
JWT_EXPIRY: 24hBest Practices
- Use clear, descriptive key names
- One secret per value
- Rotate secrets regularly
- Keep track of which VMs use which secrets
Additional Capabilities
Secrets enable the use of Docker Mods, which are tarballs of files stored on Dockerhub and/or Github Container Registry. These mods are downloaded and extracted on container boot before any init logic is run.
A Docker Mod can be specified as a single endpoint in the format user/endpoint:tag, or as an array of endpoints separated by |, such as user/endpoint:tag|user2/endpoint2:tag.
Useful Use Cases:
Preinstalling Nodejs and NPM
To preinstall Nodejs and NPM, set DOCKER_MODS=linuxserver/mods:code-server-nodejs|linuxserver/mods:code-server-npmglobal. The NODEJS_MOD_VERSION can be set to 16, 18, or 20, with a minimum of 16 and a default of 16.